
Hotel chain giant Omni Hotels & Resorts has confirmed cybercriminals stole the personal information of its customers in an apparent ransomware attack last month.
In an update on its website posted on Sunday, Omni said the stolen data includes customer names, email addresses, and postal addresses, as well as guest loyalty program information.
The company said the stolen data does not include financial information or Social Security numbers.
Ransomware gangs typically use such dark web sites to publish stolen information to extort a ransom from their victims.
A sample of the stolen data shared with DataBreaches.net matched the types of customers’ personal information that Omni said was taken.

Some of the files, which TechCrunch has seen, also contain contracts and agreements between Change Healthcare and its partners.
For Change Healthcare, there’s another complication: This is the second group to demand a ransom payment to prevent the release of stolen patient data in as many months.
UnitedHealth Group, the parent company of Change Healthcare, said there was no evidence of a new cyber incident.
What’s more likely is that a dispute between members and affiliates of the ransomware gang left the stolen data in limbo and Change Healthcare exposed to further extortion.
A Russia-based ransomware gang called ALPHV took credit for the Change Healthcare data theft.

Some of the files, which TechCrunch has seen, also contain contracts and agreements between Change Healthcare and its partners.
For Change Healthcare, there’s another complication: This is the second group to demand a ransom payment to prevent the release of stolen patient data in as many months.
UnitedHealth Group, the parent company of Change Healthcare, said there was no evidence of a new cyber incident.
What’s more likely is that a dispute between members and affiliates of the ransomware gang left the stolen data in limbo and Change Healthcare exposed to further extortion.
A Russia-based ransomware gang called ALPHV took credit for the Change Healthcare data theft.

When a hacker called the company that his gang claimed to breach, he felt the same way that most of us feel when calling the front desk: frustrated.
The recording also shows how ransomware gangs are always looking for different ways to intimidate the companies they hack.
I’m just trying to help you,” the hacker responds, growing increasingly frustrated.
“So is that Dragonforce.com?”The hacker then threatens Beth, saying they will start calling the company’s clients, employees and partners.
“Excuse me?” the hacker responds.

The State Department blamed the prolific ransomware group for targeting U.S. critical infrastructure, including healthcare services.
Last month, an affiliate group of the ALPHV/BlackCat gang took credit for a cyberattack and weeks-long outage at U.S. health tech giant Change Healthcare, which processes around one-in-three U.S. patient medical records.
The affiliate group went public after accusing the main ALPHV/BlackCat gang of swindling the contract hackers out of $22 million in ransom that Change Healthcare allegedly paid to prevent the mass leak of patient records.
Change Healthcare has said since that it ejected the hackers from its network and restored much of its systems.
U.S. health insurance giant UnitedHealth Group, the parent company of Change Healthcare, has not yet confirmed if any patient data was stolen.

American health insurance giant UnitedHealth Group has confirmed a ransomware attack on its health tech subsidiary Change Healthcare, which continues to disrupt hospitals and pharmacies across the United States.
“Based on our ongoing investigation, there’s no indication that except for the Change Healthcare systems, Optum, UnitedHealthcare and UnitedHealth Group systems have been affected by this issue.”In a post on its dark web leak site on Wednesday, ALPHV/BlackCat took credit for the cyberattack at Change Healthcare.
Change Healthcare merged with U.S. healthcare provider Optum in 2022 as part of a $7.8 billion deal under UnitedHealth Group, the largest health insurance provider in the United States.
Change Healthcare said it took much of its systems offline to expel the hackers from its systems.
Do you work at Change Healthcare, Optum or UnitedHealth and know more about the cyberattack?
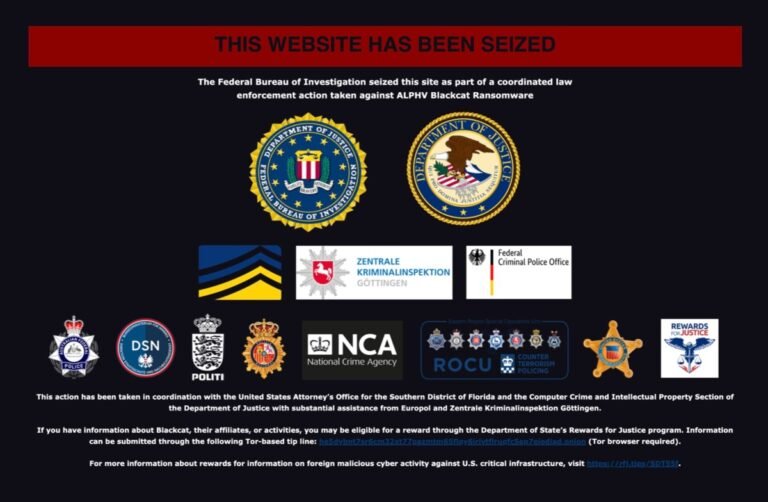
An international group of law enforcement agencies have seized the dark web leak site of the notorious ransomware gang known as ALPHV, or BlackCat.
“The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware,” a message on the gang’s dark web leak site now reads, seen by TechCrunch.
According to the splash, the takedown operation also involved law enforcement agencies from the United Kingdom, Germany and Australia.
Spokespeople for the FBI and the U.K.’s National Crime Agency did not immediately respond to TechCrunch’s requests for comment.
The ALPHV/BlackCat ransomware gang has been one of the most active and destructive in recent years.

Microsoft says it has successfully dismantled the infrastructure of a cybercrime operation that sold access to fraudulent Outlook accounts to other hackers, including the notorious Scattered Spider gang.
The group, tracked by Microsoft as “Storm-1152”, is described as a major player in the cybercrime as a service (CaaS) ecosystem, whereby criminals provide hacking and cybercrime services to other individuals or groups.
Storm-1152 created for sale approximately 750 million fraudulent Microsoft accounts through its “hotmailbox.me” service to earn “millions of dollars in illicit revenue” and cause “millions of dollars in damage to Microsoft,” according to the company.
Microsoft said it had identified several ransomware and extortion groups utilizing Storm-1162’s services, including Octo Tempest, better known as Scattered Spider.
Storm-1152 operated as a typical internet going-concern, providing training for its tools and even offering full customer support.

The recent ransomware attack that was uncovered earlier this week has resurfaced with some old tricks that hackers have used in the past. This new campaign seems to be targeting…












