
When a hacker called the company that his gang claimed to breach, he felt the same way that most of us feel when calling the front desk: frustrated.
The recording also shows how ransomware gangs are always looking for different ways to intimidate the companies they hack.
I’m just trying to help you,” the hacker responds, growing increasingly frustrated.
“So is that Dragonforce.com?”The hacker then threatens Beth, saying they will start calling the company’s clients, employees and partners.
“Excuse me?” the hacker responds.

Even ransomware gangs fail to patch vulnerabilitiesYes, even ransomware gangs are slow to patch software bugs.
Lockbit ransomware group administrative staff has confirmed with us their websites have been seized.
pic.twitter.com/SvpbeslrCd — vx-underground (@vxunderground) February 19, 2024Ransomware takedowns take a long timeThe LockBit takedown, known officially as “Operation Cronos,” was years in the making, according to European law enforcement agency Europol.
Given Kondratiev has hands in at least five different ransomware gangs, the sanctions are likely to make his life five times more difficult.
We found various Easter eggs hidden on the now-seized LockBit site.

A coalition of international law enforcement agencies, including the FBI and the U.K.’s National Crime Agency, have disrupted the operations of the prolific LockBit ransomware gang.
LockBit’s dark-web leak site — where the group publicly lists its victims and threatens to leak their stolen data unless a ransom demand is paid — was replaced with a law enforcement notice on Monday.
“This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos,’ the message reads.
The group last year claimed responsibility for attacks against aerospace giant Boeing, chipmaker TSMC, and U.K. postal giant Royal Mail.
Monday’s takedown is the latest in a series of law enforcement actions targeting ransomware gangs.

Why are ransomware gangs making so much money?
2023 was a lucrative year for ransomware gangs, fueled by an escalation in threats and tacticsFor many organizations and startups, 2023 was a rough year financially, with companies struggling to raise money and others making cuts to survive.
While 2023 was overall a bumper year for ransomware gangs, other hacker-watchers observed a drop in payments toward the end of the year.
Record-breaking ransomsWhile more ransomware victims are refusing to line the pockets of hackers, ransomware gangs are compensating for this drop in earnings by increasing the number of victims they target.
The company also predicts that a ransom payments ban would lead to the overnight creation of a large illegal market for facilitating ransomware payments.
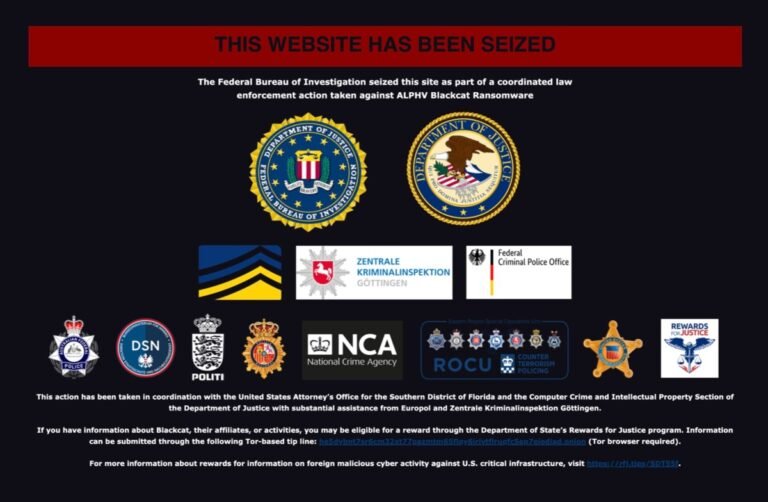
An international group of law enforcement agencies have seized the dark web leak site of the notorious ransomware gang known as ALPHV, or BlackCat.
“The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware,” a message on the gang’s dark web leak site now reads, seen by TechCrunch.
According to the splash, the takedown operation also involved law enforcement agencies from the United Kingdom, Germany and Australia.
Spokespeople for the FBI and the U.K.’s National Crime Agency did not immediately respond to TechCrunch’s requests for comment.
The ALPHV/BlackCat ransomware gang has been one of the most active and destructive in recent years.

Hive was one of the most prolific ransomware operations in recent history, with law enforcement seizing its infrastructure. This suggests that this type of malware is becoming increasingly popular and…









