
AT&T resets account passcodes after millions of customer records leak online US telco giant takes action after 2019 data breachPhone giant AT&T is reseting customer account passcodes after a huge cache of data containing millions of customer records was dumped online earlier this month, TechCrunch has exclusively learned.
A security researcher who analyzed the leaked data told TechCrunch that the encrypted account passcodes are easy to decipher.
TechCrunch held the publication of this story until AT&T could begin reseting customer account passcodes.
The leaked data includes AT&T customer names, home addresses, phone numbers, dates of birth and Social Security numbers.
The researcher double-checked their findings by looking up records in the leaked data against AT&T account passcodes known only to them.

Just five days on, LockBit announced that its operations had resumed, claiming to have restored from backups unaffected by the government takedown.
Law enforcement claiming overwhelming victory while the apparent LockBit ringleader remains at large, threatening retaliation, and targeting new victims puts the two at odds — for now.
With the apparent administrator LockBitSupp still in action — the last remaining piece of the LockBit puzzle — it’s unlikely LockBit is going away.
Ransomware gangs are known to quickly regroup and rebrand even after law enforcement disruption claims to have taken them down for good.
At the time of writing, ALPHV’s leak site remains up and running — and continues to add new victims almost daily.

Over the weekend, someone posted a cache of files and documents apparently stolen from the Chinese government hacking contractor, I-Soon.
This leak gives cybersecurity researchers and rival governments an unprecedented chance to look behind the curtain of Chinese government hacking operations facilitated by private contractors.
Since then, observers of Chinese hacking operations have feverishly poured over the files.
Also, an IP address found in the I-Soon leak hosted a phishing site that the digital rights organization Citizen Lab saw used against Tibetans in a hacking campaign in 2019.
Cary highlighted the documents and chats that show how much — or how little — I-Soon employees are paid.

A coalition of international law enforcement agencies, including the FBI and the U.K.’s National Crime Agency, have disrupted the operations of the prolific LockBit ransomware gang.
LockBit’s dark-web leak site — where the group publicly lists its victims and threatens to leak their stolen data unless a ransom demand is paid — was replaced with a law enforcement notice on Monday.
“This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos,’ the message reads.
The group last year claimed responsibility for attacks against aerospace giant Boeing, chipmaker TSMC, and U.K. postal giant Royal Mail.
Monday’s takedown is the latest in a series of law enforcement actions targeting ransomware gangs.
Astrobotic’s lunar lander will be reentering Earth’s atmosphere over a remote part of the South Pacific Ocean tomorrow afternoon, bringing to a close the failed moon landing mission.
Pittsburgh-based Astrobotic has been providing frequent updates on the Peregrine lunar lander since it launched on United Launch Alliance’s Vulcan Centaur on January 8.
The source of the anomaly was an ongoing propellant leak, which were preventing Peregrine from pointing its solar arrays at the sun.
But by the time it reenters the atmosphere tomorrow, Peregrine will have operated in space for over ten days.
Due to the propellant leak, Astrobotic said it had devised a two-step process to maneuver the spacecraft to the projected trajectory for reentry.

Astrobotic’s Peregrine lunar lander is still operating on orbit, with the company saying there is “growing optimism” that the spacecraft could survive in space longer than the current estimate.
The Pittsburgh-based startup has been releasing a series of updates to social media platform X since the spacecraft’s launch in the early hours of Monday morning.
Shortly after separating from the launch vehicle, United Launch Alliance’s Vulcan Centaur, engineers immediately started encountering issues.
But despite all odds, Peregrine has been operational in space for more than four days, and the estimated operational time remaining continues to extend.
The remaining 10 payloads on board are passive, and do not require power or communications from the spacecraft.
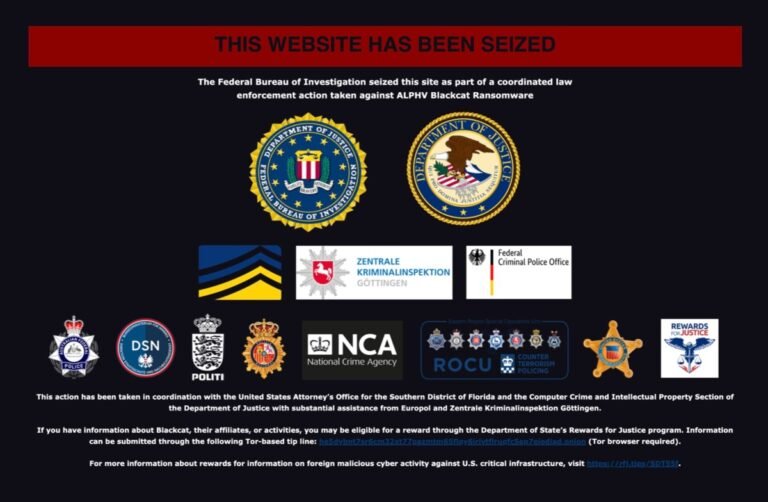
An international group of law enforcement agencies have seized the dark web leak site of the notorious ransomware gang known as ALPHV, or BlackCat.
“The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware,” a message on the gang’s dark web leak site now reads, seen by TechCrunch.
According to the splash, the takedown operation also involved law enforcement agencies from the United Kingdom, Germany and Australia.
Spokespeople for the FBI and the U.K.’s National Crime Agency did not immediately respond to TechCrunch’s requests for comment.
The ALPHV/BlackCat ransomware gang has been one of the most active and destructive in recent years.

Now in custody, the airman is facing serious charges that could land him in prison for decades. If found guilty, he could be seen as a traitor to his country…

Hive was one of the most prolific ransomware operations in recent history, with law enforcement seizing its infrastructure. This suggests that this type of malware is becoming increasingly popular and…

Twitter has been silent on the matter for months, but finally spilled the beans over an alleged data breach that exposed the contact information of millions of users. The social…













