
Just five days on, LockBit announced that its operations had resumed, claiming to have restored from backups unaffected by the government takedown.
Law enforcement claiming overwhelming victory while the apparent LockBit ringleader remains at large, threatening retaliation, and targeting new victims puts the two at odds — for now.
With the apparent administrator LockBitSupp still in action — the last remaining piece of the LockBit puzzle — it’s unlikely LockBit is going away.
Ransomware gangs are known to quickly regroup and rebrand even after law enforcement disruption claims to have taken them down for good.
At the time of writing, ALPHV’s leak site remains up and running — and continues to add new victims almost daily.

Security experts are warning that a pair of high-risk flaws in a popular remote access tool are being exploited by hackers to deploy LockBit ransomware — days after authorities announced that they had disrupted the notorious Russia-linked cybercrime gang.
In a post on Mastodon on Thursday, Sophos said that it had observed “several LockBit attacks” following exploitation of the ConnectWise vulnerabilities.
“Two things of interest here: first, as noted by others, the ScreenConnect vulnerabilities are being actively exploited in the wild.
Rogers said that Huntress has seen LockBit ransomware deployed on customer systems spanning a range of industries, but declined to name the customers affected.
The company’s website claims that the organization provides its remote access technology to more than a million small to medium-sized businesses.

Even ransomware gangs fail to patch vulnerabilitiesYes, even ransomware gangs are slow to patch software bugs.
Lockbit ransomware group administrative staff has confirmed with us their websites have been seized.
pic.twitter.com/SvpbeslrCd — vx-underground (@vxunderground) February 19, 2024Ransomware takedowns take a long timeThe LockBit takedown, known officially as “Operation Cronos,” was years in the making, according to European law enforcement agency Europol.
Given Kondratiev has hands in at least five different ransomware gangs, the sanctions are likely to make his life five times more difficult.
We found various Easter eggs hidden on the now-seized LockBit site.
The U.S. government has sanctioned two key members of LockBit, the Russian-speaking hacking and extortion gang accused of launching ransomware attacks against victims across the U.S. and internationally.
The U.S. sanctions announced Tuesday are the latest round of actions targeting the hackers behind LockBit and other prolific ransomware gangs.
In 2022, Russian-Canadian dual national Mikhail Vasiliev was arrested on allegations of launching multiple LockBit ransomware attacks.
A third suspect, Russian national Mikhail Pavlovich Matveev, was accused of involvement in several ransomware operations, including LockBit.
Security researchers say that ransomware victims who pay a ransom are more likely to experience subsequent ransomware attacks.

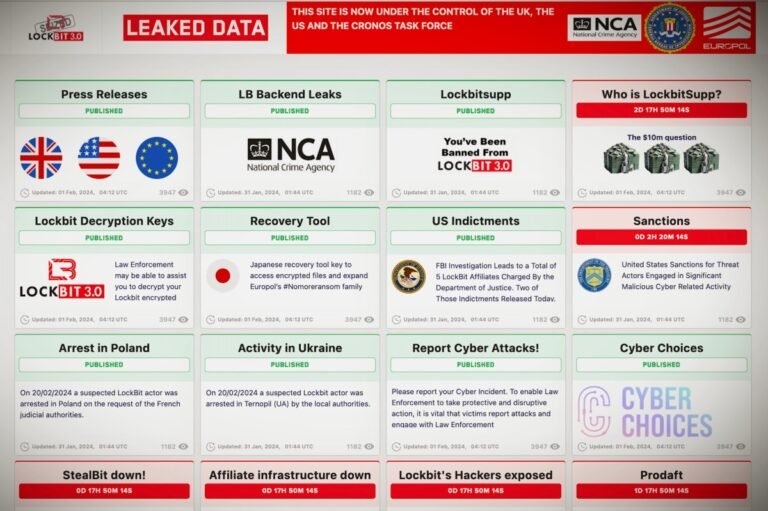
A coalition of international law enforcement agencies, including the FBI and the U.K.’s National Crime Agency, have disrupted the operations of the prolific LockBit ransomware gang.
LockBit’s dark-web leak site — where the group publicly lists its victims and threatens to leak their stolen data unless a ransom demand is paid — was replaced with a law enforcement notice on Monday.
“This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos,’ the message reads.
The group last year claimed responsibility for attacks against aerospace giant Boeing, chipmaker TSMC, and U.K. postal giant Royal Mail.
Monday’s takedown is the latest in a series of law enforcement actions targeting ransomware gangs.








