The United States government has taken action against two prominent members of LockBit, a Russian-speaking hacking and extortion group that has been carrying out ransomware attacks against targets in the US and abroad.
The US Treasury announced on Tuesday that it has imposed sanctions on Artur Sungatov and Ivan Gennadievich Kondratiev, both Russian nationals who have been indicted for their alleged involvement with LockBit. Kondratiev has also been linked to other ransomware gangs, including REvil, RansomEXX, and Avaddon.
Deputy Secretary of the Treasury Wally Adeyemo stated, “We will not tolerate any attempts to extort and steal from our citizens and institutions. The US will use all available tools to hold accountable those responsible for these malicious cyber activities.”
The sanctions prohibit any US businesses or individuals from transacting or making payments to those listed, a tactic intended to discourage victims from paying the hackers’ ransom demands.
This move to sanction individual hackers, rather than entire groups, aims to make it more difficult for them to turn a profit from ransomware attacks, as they are frequently able to rebrand or change names to evade sanctions.
Any violations of US sanctions can result in severe penalties and even criminal prosecution for companies or individuals involved in paying a sanctioned hacker.
The sanctions were announced just hours after US and UK authorities revealed a global law enforcement operation to disrupt LockBit’s operations. As part of this operation, authorities seized LockBit’s infrastructure, including the group’s dark web leak site, where victims’ stolen data was published unless a ransom was paid.
US prosecutors have accused LockBit of carrying out at least 2,000 ransomware attacks against victims in the US and around the world, raking in over $120 million in ransom payments since its inception in 2019.
The group has claimed responsibility for numerous high-profile attacks, such as targeting the California Department of Finance, the UK’s Royal Mail, and the US dental insurance company MCNA, compromising the personal information of millions of individuals.
This is just the latest round of actions taken by the US government against the hackers behind LockBit and other prolific ransomware groups.
In 2022, Russian-Canadian dual national Mikhail Vasiliev was arrested for his involvement in multiple LockBit attacks. The following year, Ruslan Magomedovich Astamirov was also arrested under similar allegations. Both suspects are currently in custody awaiting trial.
In 2023, Russian national Mikhail Pavlovich Matveev, who was linked to several ransomware operations, including LockBit, was sanctioned by the US government. Despite the monetary reward of $10 million for information leading to his arrest, Matveev has yet to be apprehended.
The alleged ringleader of LockBit, known by the moniker LockBitSupp, has not been named by the US government in their recent announcement. According to the now-seized LockBit dark web leak site, law enforcement is expected to release more information about this individual on Friday, including a $10 million reward for any information that leads to their location or identification.
The US government currently does not prohibit victims from paying a ransom, although the FBI does strongly advise against it due to the potential for fueling future attacks. Research has also shown that victims who do pay a ransom are more likely to be targeted again by ransomware attacks.
To learn more, visit TechCrunch for the latest news on technology and cybersecurity.
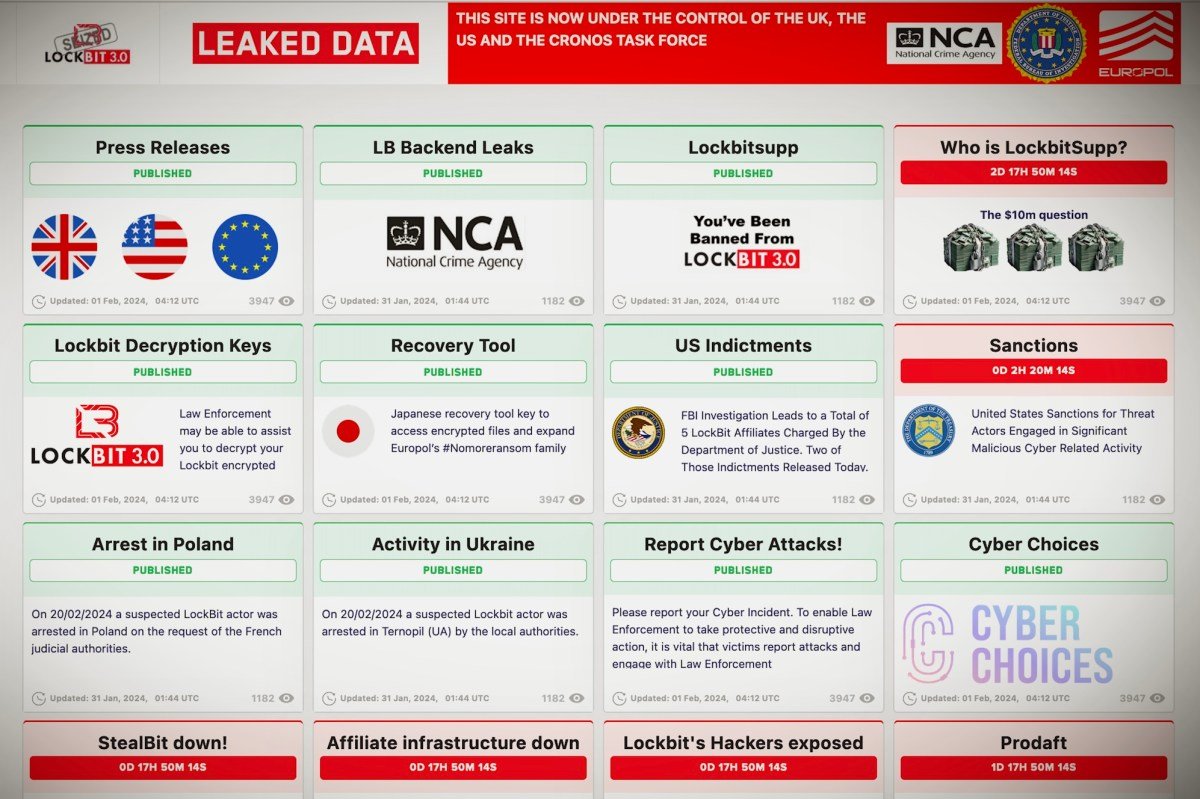








[…] has conducted an extensive operation that has rooted out LockBit, the notorious Russia-linked ransomware gang responsible for causing chaos in numerous businesses, hospitals, and governments worldwide […]