
Hackers are threatening to publish a huge stolen sanctions and financial crimes watchlist The stolen World-Check database contains 5.3 million recordsA financially motivated hacking group says it has stolen a confidential database containing millions of records that companies use for screening potential customers for links to sanctions and financial crime.
The hackers, which call themselves GhostR, said they stole 5.3 million records from the World-Check screening database in March and are threatening to publish the data online.
A portion of the stolen data, which the hackers shared with TechCrunch, includes individuals who were sanctioned as recently as this year.
The incident involves a third party’s data set, which includes a copy of the World-Check data file.
Banking giant HSBC shut down bank accounts belonging to several prominent British Muslims after the World-Check database branded them with “terrorism” tags.

In its previous price list, published in 2019, the highest payouts that Crowdfense was offering were $3 million for Android and iOS zero-days.
In a report last month, Google said it saw hackers use 97 zero-day vulnerabilities in the wild in 2023.
Spyware vendors, which often work with zero-day brokers, were responsible for 75 percent of zero-days targeting Google products and Android, according to the company.
Zero-day brokers, as well as spyware companies like NSO Group and Hacking Team have often been criticized for selling its products to unsavory governments.
“All the companies and governments directly sanctioned by the USA are excluded.”At least one company, spyware consortium Intellexa, is on Crowdfense’s particular blocklist.

Global Screening Services (GSS), a London-based regulatory compliance platform that helps financial institutions meet their global sanctions obligations, has raised $47 million in a round of funding.
The raise comes amid a spike in economic sanctions, with the U.S. issuing trade-restrictions and asset-blocking against states including Russia, China, Iran and more.
The company actually raised a similar amount of funding last year from big-name backers including Japan’s Mitsubishi UFJ Financial Group (MUFG), one of the world’s largest banks.
Banks often find themselves at the forefront of sanctions enforcement, given their role in controlling the flow of money around the globe.
GSS sells a sanctions-screening platform to help banks and other financial institutions comply with regulations.

Earlier this week, the U.S. government announced sanctions against the founder of a controversial government spyware maker, Tal Dilian, and his business associate, Sara Aleksandra Fayssal Hamou.
If the U.S. government thinks someone sold spyware to authoritarians and dictators, or their company’s spyware was used against the wrong targets, it will go directly after the people running those spyware companies.
And people who used to work in the government spyware industry expressed concern.
That’s big,” said a former head of a spyware maker that sold to governments, when TechCrunch shared the news of the sanctions with him.
According to a third person working in the spyware industry, the sanctions against Dilian and his business associate Hamou should make the whole market have a moment of reflection.
The U.S. government announced Tuesday sanctions against the founder of the notorious spyware company Intellexa and one of his business partners.
This is the first time the U.S. government has targeted specific people, in addition to companies, with sanctions related to the misuse of commercial spyware.
These sanctions will impact Dilian and Hamou specifically, but they will also send a message to other people involved in the spyware industry.
“If I’m a mercenary spyware company, I should be getting really worried,” added Scott-Railton.
And earlier this year, the U.S. government announced that the State Department could impose visa restrictions to people believed to have been involved or facilitated the abuse of commercial spyware around the world.
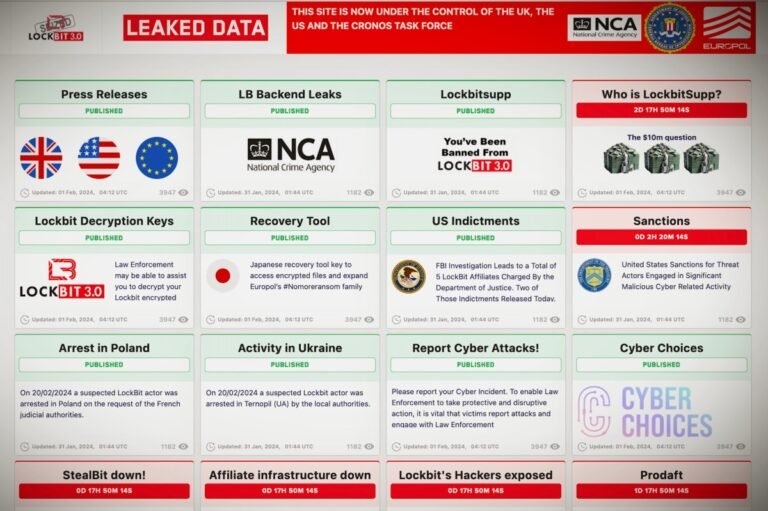
The U.S. government has sanctioned two key members of LockBit, the Russian-speaking hacking and extortion gang accused of launching ransomware attacks against victims across the U.S. and internationally.
The U.S. sanctions announced Tuesday are the latest round of actions targeting the hackers behind LockBit and other prolific ransomware gangs.
In 2022, Russian-Canadian dual national Mikhail Vasiliev was arrested on allegations of launching multiple LockBit ransomware attacks.
A third suspect, Russian national Mikhail Pavlovich Matveev, was accused of involvement in several ransomware operations, including LockBit.
Security researchers say that ransomware victims who pay a ransom are more likely to experience subsequent ransomware attacks.

The U.S. government sanctioned a Russian national for allegedly playing a “pivotal role” in the ransomware attack against Australian health insurance giant Medibank that exposed the sensitive information of almost 10 million patients.
The breach is believed to have impacted several high-profile Medibank customers, including senior Australian government lawmakers.
The U.S. Treasury Department sanctioned Ermakov shortly after the Australian government imposed first-of-its-kind sanctions against the Russian national.
According to the U.S. Treasury, REvil ransomware has been deployed on approximately 175,000 computers worldwide, garnering at least $200 million in ransom payments.
The FSB’s surprise operation came just months after the U.S. Department of Justice charged a 22-year-old Ukrainian citizen linked to the REvil ransomware gang due to his alleged role in the Kaseya attack.










