
Palo Alto Networks urged companies this week to patch against a newly discovered zero-day vulnerability in one of its widely used security products, after malicious hackers began exploiting the bug to break into corporate networks.
Because the vulnerability allows hackers to gain complete control of an affected firewall over the internet without authentication, Palo Alto gave the bug a maximum severity rating.
The ease with which hackers can remotely exploit the bug puts thousands of companies that rely on the firewalls at risk from intrusions.
Adding another complication, Palo Alto initially suggested disabling telemetry to mitigate the vulnerability, but said this week that disabling telemetry does not prevent exploitation.
Security firm Volexity, which first discovered and reported the vulnerability to Palo Alto, said it found evidence of malicious exploitation going back to March 26, some two weeks before Palo Alto released fixes.

I’m getting hacked, I’m getting hacked bro, I’m getting hacked,” said one of the players allegedly compromised during a live stream of the gameplay.
On Tuesday, Respawn, the studio that develops Apex Legends posted a statement on X (formerly Twitter), addressing the incidents.
Conor Ford, who works on Apex Legends security team, wrote on X that he and his colleagues are working to address the issues.
Or other video game hacking incidents?
Or other video game hacking incidents?

A bug in an Irish government website that exposed COVID-19 vaccination records took two years to publicly discloseThe Irish government fixed a vulnerability two years ago in its national COVID-19 vaccination portal that exposed the vaccination records of around a million residents.
But details of the vulnerability weren’t revealed until this week after attempts to coordinate public disclosure with the government agency stalled and ended.
Security researcher Aaron Costello said he discovered the vulnerability in the COVID-19 vaccination portal run by the Irish Health Service Executive (HSE) in December 2021, a year after mass vaccinations against COVID-19 began in Ireland.
Costello’s public disclosure marks more than two years since first reporting the vulnerability.
His blog post included a multi-year timeline revealing a back and forth between various government departments that were unwilling to take claim to public disclosure.
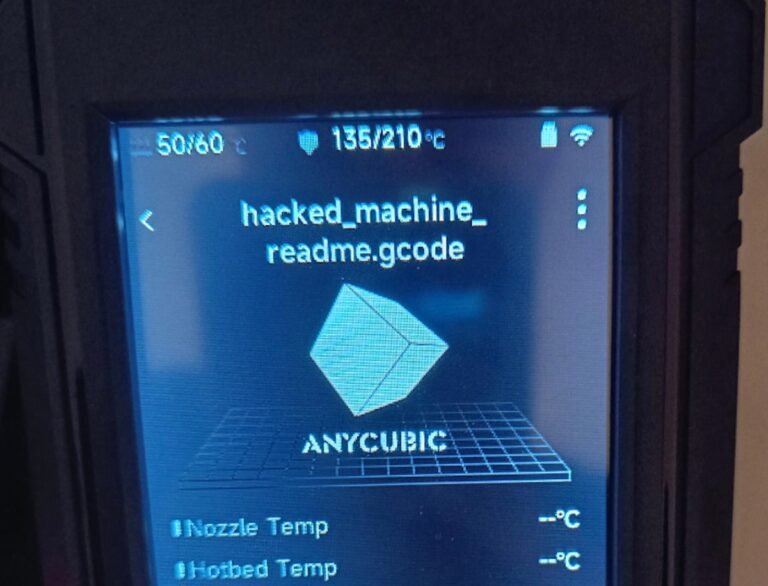
Anycubic users say their 3D printers were hacked to warn of a security flawAnycubic customers are reporting that their 3D printers have been hacked and now display a message warning of an alleged security flaw in the company’s systems.
Feel free to disconnect your printer from the internet if you don’t wanna get hacked by a bad actor!
You have not been harmed in any way.”The text file described an unspecified vulnerability in Anycubic’s MQTT service, which allegedly allows the ability to “connect and control” customer 3D printers that are connected to the internet.
The person who authored the text file claimed they sent the message to 2.9 million Anycubic 3D printers.
“Disconnect your printer from the internet until anycubic patches this issue,” the text file reads.

Researchers warn high-risk ConnectWise flaw under attack is ’embarrassingly easy’ to exploit “I can’t sugarcoat it — this shit is bad," said Huntress' CEOSecurity experts are warning that a high-risk vulnerability in a widely used remote access tool is “trivial and embarrassingly easy” to exploit, as the software’s developer confirms malicious hackers are actively exploiting the flaw.
The maximum severity-rated vulnerability affects ConnectWise ScreenConnect (formerly ConnectWise Control), a popular remote access software that allows managed IT providers and technicians to provide real-time remote technical support on customer systems.
Cybersecurity company Huntress on Wednesday published an analysis of the actively exploited ConnectWise vulnerability.
ConnectWise also released a fix for a separate vulnerability affecting its remote desktop software.
The U.S. agencies also observed hackers abusing remote access software from AnyDesk, which was earlier this month forced to reset passwords and revoke certificates after finding evidence of compromised production systems.

Log4j, maybe more than any other recent security issue in recent years, thrust software supply chain security into the limelight, with even the White House weighing in.
Some of those may be in libraries that aren’t even used when the container is in production, but they are vulnerabilities nevertheless.
According to Slim.ai‘s latest Container Report, the average organization now deploys well over 50 containers from their vendors every month (and almost 10% deploy more than 250).
Yet only 12% of the security leaders who responded to Slim.ai’s survey said they were able to achieve their own vulnerability remediation goals.
Most companies see some disruptions multiple times a week because they detect a vulnerability in a production container, for example.

Comcast has confirmed that hackers exploiting a critical-rated security vulnerability accessed the sensitive information of almost 36 million Xfinity customers.
Hackers have used the CitrixBleed vulnerability to hack into big-name victims, including aerospace giant Boeing, the Industrial and Commercial Bank of China, and international law firm Allen & Overy.
The notice doesn’t say how many Xfinity customers have been impacted, and Comcast spokesperson Joel Shadle declined to say when asked by TechCrunch.
In a filing with Maine’s attorney general, Comcast confirmed that almost 35.8 million customers are affected by the breach.
Comcast’s latest earnings report shows the company has over 32 million broadband customers, suggesting this breach has impacted most, if not all Xfinity customers.










