It’s not uncommon for platforms like Patreon to offer creators a means of receiving funds from their supporters. However, this recently fixed security bug shows that even privacy-focused platforms can put creators’ private information at risk. This vulnerability allowed anyone with access to a creator’s account details to transfer money out of their account without the creator’s consent or knowledge. This could have potentially led to the theft of funds belonging to the creators, and increased repayments owed by them as a result.
With Throne, fans can purchase items recommended by their favorite creators without ever having toRLISE to the creator’s personally identifiable information. This eliminates the need for creators to have to worry about unworthy or harassing fans, and instead allows them to focus on creating quality content.
Trophae is a new website that allows online creators, like streamers and gamers, to publish a wishlist of gifts that supporters can buy. Throne acts as the go-between, processing the payment and ensuring that the item gets sent. This is an innovative way for online creators to raise money for themselves and their followers, without having to reveal their personal information.
After the creator users’ private home addresses were exposed by the vulnerability, they received death threats and obscene messages on social media. However, they are confident that their stance against big data privacy violations will continue undeterred.
Zerforschung is known for its impressive discovery of major security bugs in social media platform Hive. This year, the collective has discovered another major bug in email platform MailChimp that could allow unauthorized access to users’ emails.
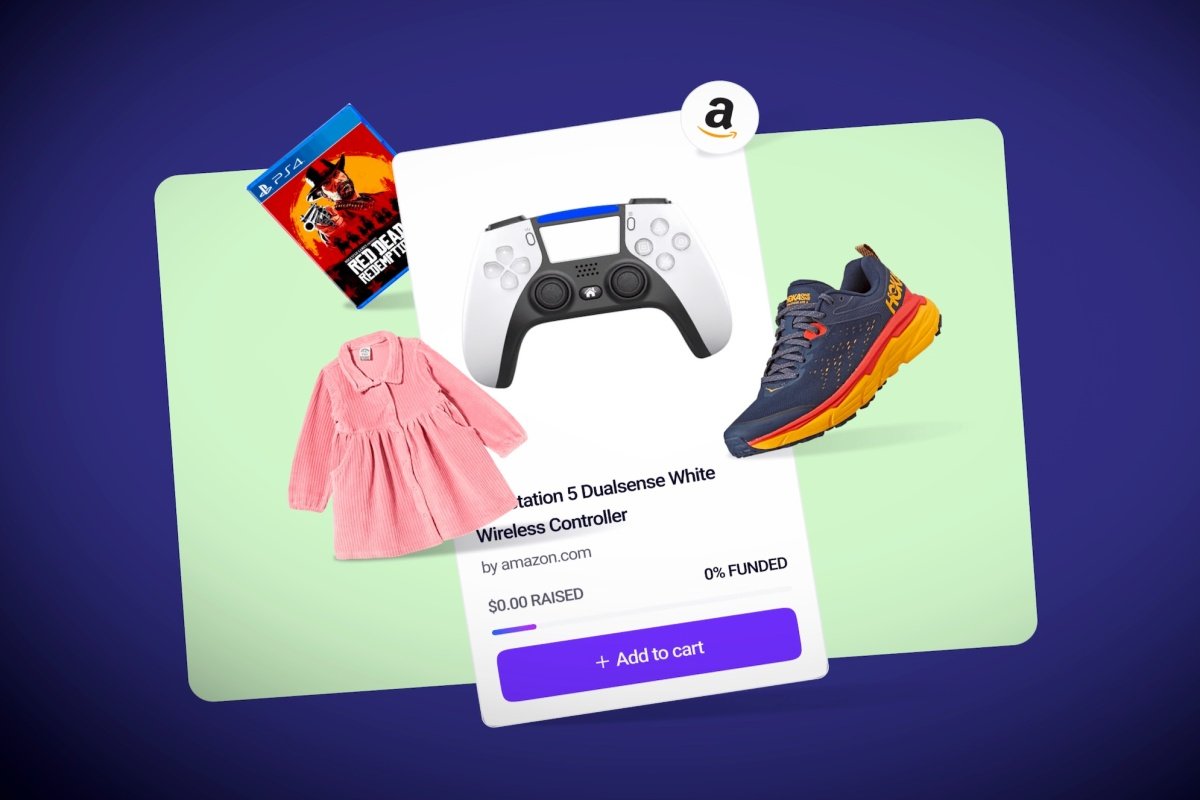
According to Zerforschung, their discovery could have serious consequences for the company’s users if it wasn’t fixed soon. If someone were to gain access to the database, they could potentially access personal information such as Amazon login credentials and past purchase data. Given that the database is publicly available on Google’s Firebase platform, this vulnerability presents a serious risk to the company’s customers. While this vulnerability has already been fixed by Zerforschung, it is important that companies take precautions to protect their users’ data even in cases where a security breach does not result in adverse consequences for individuals.
Session cookies are a common target for hackers because they can be used to log in as if the user was still logged in. This can make it more difficult to detect when someone other than the user is misusing a session cookie.
The Amazon session cookies that the security researchers found were easily accessible on Throne’s account allowed them to access all of his orders and the personal information of the creators of those orders. This could potentially put these individuals at risk if their information was accessed by someone who had access to Throne’s Amazon account.
This bug could have led to the exposure of thousands of creators’ addresses and names if they had been using Throne in a video call. This is a serious issue that needs to be fixed as soon as possible, so that people who use Throne do not risk their personal information becoming public.
throne’s acknowledgement of the security lapse is a swift response that shows the company’s dedication to keeping its users safe. By quickly fixing the bug and informing researchers, Throne has shown that it takes user safety seriously.
According to Throne, the misconfigured Firestore rules made it possible for the security researchers to read some data which should not have been available such as the blocked IP addresses we maintain for fraud prevention purposes and session cookies for a small subset of our merchant accounts. This incident serves as a reminder that even small changes to your app’s code can have disastrous consequences, and that developers need to take precautions to ensure their apps are secure from malicious actors.
Zerforschung alleges that Throne’s assertion that there was no risk and no unknown party had viewed any data is false, as the company did not ask the collective for their IP addresses that could have been used to investigate the incident. This lack of transparency raises questions about Throne’s assertion of security and undermines public trust in their technology.
Throne’s logs could reveal who accessed or exfiltrated its data, but no one knows for sure if anyone else accessed or exfiltrated the information. If Zerforschung found the bug, it’s possible that malicious actors have discovered it too. Throne doesn’t seem to have the ability to determine what data was viewed, but this information is still valuable in security investigations.
Although Throne claimed that there was no data risk associated with the acquisition of Facebook user data, Zerforschung proved otherwise. The expert said that there is a real possibility that user data could have been compromised by the acquisition, and Facebook should make sure it takes all necessary steps to ensure its users are properly protected.
Given Throne’s history of publishing blog posts on data privacy, and the fact that it has refused to comment on our specific questions or provide the name of the alleged data privacy expert mentioned in its blog post, it seems clear that Throne neither understands nor cares about data privacy concerns.
Perhaps Becker was not aware of Zerforschung’s findings when he made the decision to disclose creators’ home addresses. In fact, it is possible that this information was never disclosed to him at all, and instead came from a third party who leaked the information. Alternatively, Becker may have believed that disclosing the address would help create a better environment for creators on Patreon. However, it seems as though this strategy backfired – many