
Last week, Australian authorities sounded the alarm saying they had become aware of “successful compromises of several companies utilising Snowflake environments,” without naming the companies.
TechCrunch has this week seen hundreds of alleged Snowflake customer credentials that are available online for cybercriminals to use as part of hacking campaigns, suggesting that the risk of Snowflake customer account compromises may be far wider than first known.
When we checked the web addresses of the Snowflake environments — often made up of random letters and numbers — we found the listed Snowflake customer login pages are publicly accessible, even if not searchable online.
In our checks, we found that these Snowflake login pages redirected to Live Nation (for Ticketmaster) and Santander sign-in pages.
There is some evidence to suggest that several employees with access to their company’s Snowflake environments had their computers previously compromised by infostealing malware.

Last month, a hacker wreaked havoc during an esports tournament of the popular shooter game Apex Legends, hacking two well-known streamers mid-game to make it look like they were using cheats.
“The exploit I’ve used in [Apex Legends Global Series] is fully patched,” the hacker who goes by Destroyer2009 said in an online chat.
Or other video game hacking incidents?
Or other video game hacking incidents?
Destroyer2009’s hacks were high-profile, disruptive, and caused a big stir in the Apex Legends community.

Palo Alto Networks urged companies this week to patch against a newly discovered zero-day vulnerability in one of its widely used security products, after malicious hackers began exploiting the bug to break into corporate networks.
Because the vulnerability allows hackers to gain complete control of an affected firewall over the internet without authentication, Palo Alto gave the bug a maximum severity rating.
The ease with which hackers can remotely exploit the bug puts thousands of companies that rely on the firewalls at risk from intrusions.
Adding another complication, Palo Alto initially suggested disabling telemetry to mitigate the vulnerability, but said this week that disabling telemetry does not prevent exploitation.
Security firm Volexity, which first discovered and reported the vulnerability to Palo Alto, said it found evidence of malicious exploitation going back to March 26, some two weeks before Palo Alto released fixes.

It’s against this backdrop that Evolution Equity Partners, a growth capital investment firm based in NYC, on Tuesday launched a $1.1 billion cybersecurity and AI fund, the third such fund in Evolution’s history.
The fund, called Evolution Technology Fund III, was oversubscribed, with participation from existing and new endowments, sovereign investors, insurance companies, foundations, fund of funds, family offices and angels.
“The Evolution Technology Fund III has already backed fifteen leading cybersecurity companies, initiating its investment period over 12 months ago,” Seewald said.
“We believe that provides private markets investors with diversified exposure to cybersecurity opportunities.”ESG will be another factor, according to Seewald.
Evolution’s 30-person teams manages around $2 billion in assets and has backed 60 companies to date; its previous fund was $400 million.

U.S. cybersecurity agency CISA is warning Sisense customers to reset their credentials and secrets after the data analytics company reported a security incident.
CISA said it urges Sisense customers to “reset credentials and secrets potentially exposed to, or used to access, Sisense services” and to report any suspicious activity involving the use of compromised credentials to the agency.
Founded in 2004, Sisense develops business intelligence and data analytics software for big companies, including telcos, airlines and tech giants.
Companies like Sisense rely on using credentials, such as passwords and private keys, to access a customer’s various stores of data for analysis.
With access to these credentials, an attacker could potentially also access a customer’s data.
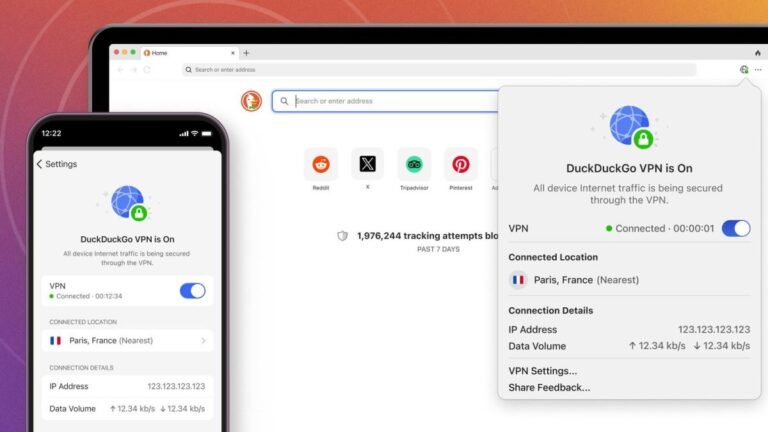
Privacy-focused consumer tech company DuckDuckGo launched a new Privacy Pro subscription on Thursday that bundles a VPN service, personal information removal, and identity theft restoration.
This is the company’s first move towards a subscription service built into the DuckDuckGo browser.
With personal information removal service, DuckDuckGo scans dozens of data broker sites to find details like your name and address.
(At that time, Removaly’s founder, Kyle Krzeski, posted on X that a privacy company acquired the startup without naming it.)
The third feature of DuckDuckGo’s privacy pro plan is identity theft restoration, where an advisor would help you recover your identity-related loss around the clock.

After leaving Nvidia in 2010, Kumar pivoted to cybersecurity, eventually co-founding Fortanix, a cloud data security platform.
Leveraging AI, Simbian can automatically orchestrate and operate existing security tools, finding the right configurations for each product by taking into account a company’s priorities and thresholds for security, informed by their business requirements.
A separate study found that organizations now juggle on average 76 different security tools, leading IT teams and leaders to feel overwhelmed.
In addition to automatically configuring a company’s security tools, the Simbian platform attempts to respond to “security events” by letting customers steer security while taking care of lower-level details.
But that assumes Simbian’s AI doesn’t make mistakes, a tall order, given that it’s well established that AI is error-prone.
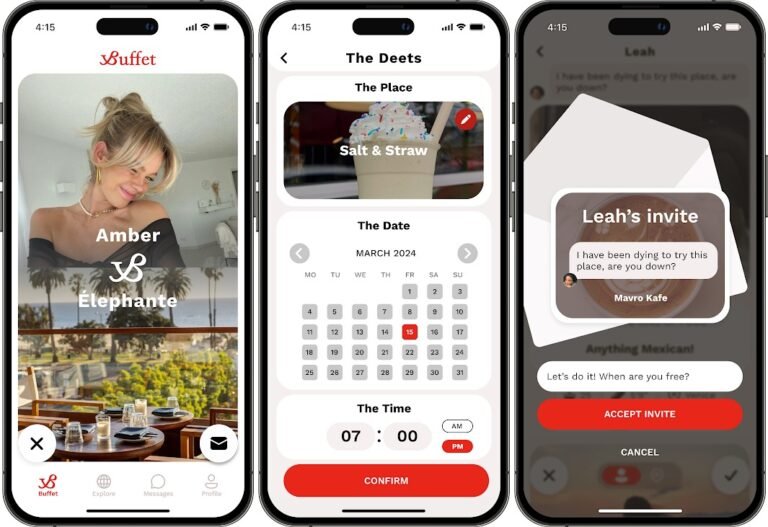
A new app called Buffet is aiming to address the loneliness epidemic by helping users meet new people by quickly matching them with a person and a place to meet up (Think Tinder + OpenTable).
Buffet aims to help users meet likeminded individuals, whether they’re looking for a new friend, romantic partner or gym buddy.
So we put one foot in front of the other and stared building Buffet.”To get started with Buffet, users enter five of their interests, such as motorcycles, horseback riding or reading.
Buffet encourages people to go beyond a chatbox and digital communication and actually meet up in the real world.
Hacking believes that if Buffet can win over the average 25-year-old female professional, it can win over anyone.

Seven open source foundations are coming together to create common specifications and standards for Europe’s Cyber Resilience Act (CRA), regulation adopted by the European Parliament last month.
And this is what the seven open source foundations are coming together for now.
By coming together as one, this should go some way toward treating open source software development as a single “thing” bound by the same standards and processes.
Throw into the mix other proposed regulation, including the Securing Open Source Software Act in the U.S., and it’s clear that the various foundations and “open source stewards” will come under greater scrutiny for their role in the software supply chain.
“The open source community and the broader software industry now share a common challenge: legislation has introduced an urgent need for cybersecurity process standards.

Death, taxes, and regular, terrifying cybersecurity leaks.
Those are the facts of life, as the latest AT&T data breach is teaching us yet again.
A TechCrunch investigation into leaked customer data from the American telco giant has led to AT&T resetting certain customer account passcodes to prevent them from being at risk.
The root of the security weakness is a massive, and AT&T’s data breach included a leaked dataset concerning more than seventy million former and current AT&T account holders.
Only a fraction are still current, but the scale of the leaked dataset that TechCrunch dug into makes it plain that despite huge amounts of work and investment, there are still regular, exploitable, and dangerous for consumers.













