
The State Department blamed the prolific ransomware group for targeting U.S. critical infrastructure, including healthcare services.
Last month, an affiliate group of the ALPHV/BlackCat gang took credit for a cyberattack and weeks-long outage at U.S. health tech giant Change Healthcare, which processes around one-in-three U.S. patient medical records.
The affiliate group went public after accusing the main ALPHV/BlackCat gang of swindling the contract hackers out of $22 million in ransom that Change Healthcare allegedly paid to prevent the mass leak of patient records.
Change Healthcare has said since that it ejected the hackers from its network and restored much of its systems.
U.S. health insurance giant UnitedHealth Group, the parent company of Change Healthcare, has not yet confirmed if any patient data was stolen.

The U.K. government has blamed China for a 2021 cyberattack that compromised the personal information of millions of U.K. voters.
The data breach began as early as 2021 but wasn’t detected until a year later.
Dowden said that a separate attempted cyberattack by a China-backed hacking group targeted the email accounts of U.K. lawmakers in 2021, but that parliamentary authorities mitigated the attempted breaches before any email accounts were compromised.
The Norwegian government previously attributed a 2018 data breach on its systems to APT31.
In 2020, Google security researchers linked APT31 to the targeting of email accounts belonging to the Trump and Biden presidential campaigns.

The Pokemon Company said it detected hacking attempts against some of its users and reset those user account passwords.
A spokesperson for the company said there was no breach, just a series of hacking attempts against some users.
To protect our customers we have reset some passwords which prompted the message,” said Daniel Benkwitt, a Pokemon Company spokesperson.
The description of the Pokemon account breaches sounds like credential stuffing, where malicious hackers use usernames and passwords stolen from other breaches and reuse them on other sites.
For its part, the Pokemon Company does not allow its users to enable two-factor on their accounts, when TechCrunch checked.

On Friday, Microsoft said Russian government hackers continue to break into its systems using information obtained during a hack last year.
This time, the Russian hackers dubbed Midnight Blizzard have targeted Microsoft’s source code and other internal systems, the company said.
This has included access to some of the company’s source code repositories and internal systems,” Microsoft wrote in a blog post.
This new intrusion comes after Microsoft revealed in January that Russian government hackers had broken into the company’s systems last November.
Midnight Blizzard is believed to be a hacking group working for Russia’s Foreign Intelligence Service, known by its Russian initials, SVR.

As cybercriminals continue to reap the financial rewards of their attacks, talk of a federal ban on ransom payments is getting louder.
Since then, just as talk of a potential ransom payment ban has gotten louder, so has the ransomware activity.
Is a ban on ransom payments the solution?
For a ban on ransom payments to be successful, international and universal regulation would need to be implemented — which, given varying international standards around ransom payments, would be almost impossible to enforce.
Given the brazen nature of these attackers, it’s unlikely that they would be deterred by a ban on ransom payments.

The U.S. National Security Agency has confirmed that hackers exploiting flaws in Ivanti’s widely used enterprise VPN appliance have targeted organizations across the U.S. defense sector.
Confirmation that the NSA is tracking these cyberattacks comes days after Mandiant reported that suspected Chinese espionage hackers have made “mass attempts” to exploit multiple vulnerabilities impacting Ivanti Connect Secure, the popular remote access VPN software used by thousands of corporations and large organizations worldwide.
Mandiant said earlier this week that the China-backed hackers tracked as a threat group it calls UNC5325 had targeted organizations across a variety of industries.
This includes the U.S. defense industrial base sector, a worldwide network of thousands of private sector organizations that provide equipment and services to the U.S. military, Mandiant said, citing earlier findings from security firm Volexity.
Akamai said in an analysis published last week that hackers are launching approximately 250,000 exploitation attempts each day and have targeted more than 1,000 customers.

Security researchers say a pair of easy-to-exploit flaws in a popular remote access tool used by more than a million companies around the world are now being mass-exploited, with hackers abusing the vulnerabilities to deploy ransomware and steal sensitive data.
ConnectWise first disclosed the flaws on February 19 and urged on-premise customers to install security patches immediately.
Finnish cybersecurity firm WithSecure said in a blog post Monday that its researchers have also observed “en-mass exploitation” of the ScreenConnect flaws from multiple threat actors.
It’s not yet known how many ConnectWise ScreenConnect customers or end users are affected by these vulnerabilities, and ConnectWise spokespeople did not respond to TechCrunch’s questions.
The company’s website claims that the organization provides its remote access technology to more than a million small to medium-sized businesses that manage over 13 million devices.

Security experts are warning that a pair of high-risk flaws in a popular remote access tool are being exploited by hackers to deploy LockBit ransomware — days after authorities announced that they had disrupted the notorious Russia-linked cybercrime gang.
In a post on Mastodon on Thursday, Sophos said that it had observed “several LockBit attacks” following exploitation of the ConnectWise vulnerabilities.
“Two things of interest here: first, as noted by others, the ScreenConnect vulnerabilities are being actively exploited in the wild.
Rogers said that Huntress has seen LockBit ransomware deployed on customer systems spanning a range of industries, but declined to name the customers affected.
The company’s website claims that the organization provides its remote access technology to more than a million small to medium-sized businesses.
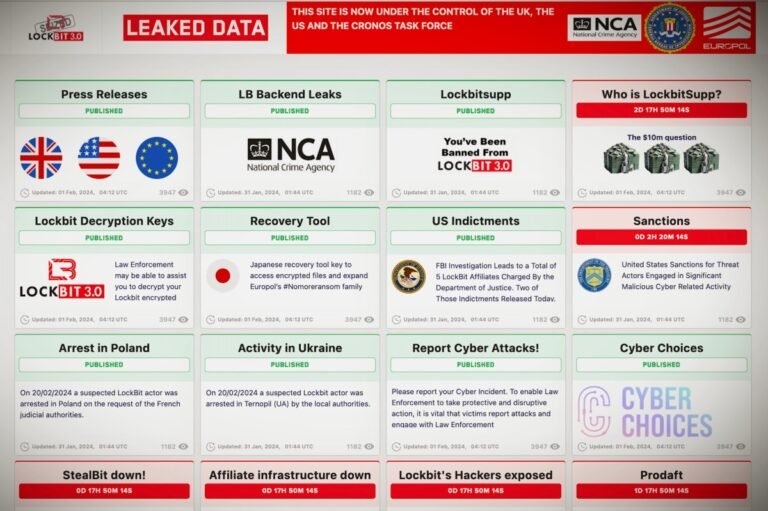
The U.S. government has sanctioned two key members of LockBit, the Russian-speaking hacking and extortion gang accused of launching ransomware attacks against victims across the U.S. and internationally.
The U.S. sanctions announced Tuesday are the latest round of actions targeting the hackers behind LockBit and other prolific ransomware gangs.
In 2022, Russian-Canadian dual national Mikhail Vasiliev was arrested on allegations of launching multiple LockBit ransomware attacks.
A third suspect, Russian national Mikhail Pavlovich Matveev, was accused of involvement in several ransomware operations, including LockBit.
Security researchers say that ransomware victims who pay a ransom are more likely to experience subsequent ransomware attacks.

Why are ransomware gangs making so much money?
2023 was a lucrative year for ransomware gangs, fueled by an escalation in threats and tacticsFor many organizations and startups, 2023 was a rough year financially, with companies struggling to raise money and others making cuts to survive.
While 2023 was overall a bumper year for ransomware gangs, other hacker-watchers observed a drop in payments toward the end of the year.
Record-breaking ransomsWhile more ransomware victims are refusing to line the pockets of hackers, ransomware gangs are compensating for this drop in earnings by increasing the number of victims they target.
The company also predicts that a ransom payments ban would lead to the overnight creation of a large illegal market for facilitating ransomware payments.













