
Streaming giant Roku has confirmed a second security incident in as many months, with hackers this time able to compromise more than half a million Roku user accounts.
In a statement Friday, the company said about 576,000 user accounts were accessed using a technique known as credential stuffing, where malicious hackers use usernames and passwords stolen from other data breaches and reuse the logins on other sites.
Roku said in fewer than 400 account breaches, the malicious hackers made fraudulent purchases of Roku hardware and streaming subscriptions using the payment data stored in those users’ accounts.
Two-factor authentication prevents credential stuffing attacks by adding an additional layer of security to online accounts.
By prompting a user to enter a time-sensitive code along with their username and password, malicious hackers cannot break into a user’s account with just a stolen password.

Documentation startup Mintlify says dozens of customers had GitHub tokens exposed in a data breach at the start of the month and publicly disclosed last week.
Mintlify helps developers create documentation for their software and source code by requesting access and tapping directly into the customer’s GitHub source code repositories.
These private tokens allow GitHub users to share their account access with third parties apps, including companies like Mintlify.
“The targets of this attack were GitHub tokens of our users,” Wang told TechCrunch by email.
We are currently working with GitHub and our customers to uncover if any of the other tokens were used by the attacker,” Wang said.

U.S. healthcare technology giant Change Healthcare has confirmed a cyberattack on its systems.
Most of the login pages for Change Healthcare are inaccessible or offline when TechCrunch checked at the time of writing.
Michigan local newspaper the Huron Daily Tribune is reporting that local pharmacies are experiencing outages due to the Change Healthcare cyberattack.
Change Healthcare is one of the largest healthcare technology companies in the United States.
Both Optum and Change Healthcare are owned by health insurance giant UnitedHealth Group.

About 16.6 million LoanDepot customers had their “sensitive personal” information” stolen in a cyberattack earlier this month, which the loan and mortgage giant has described as ransomware.
The loan company said in a filing with federal regulators on Monday that it would notify the affected customers of the data breach.
LoanDepot did not say what kind of sensitive and personal customer data was stolen.
When reached by email, LoanDepot spokesperson Jonathan Fine declined to tell TechCrunch what specific types of customer data was taken.
LoanDepot said it has “not yet determined” whether the cybersecurity incident will materially impact the company’s financial condition.
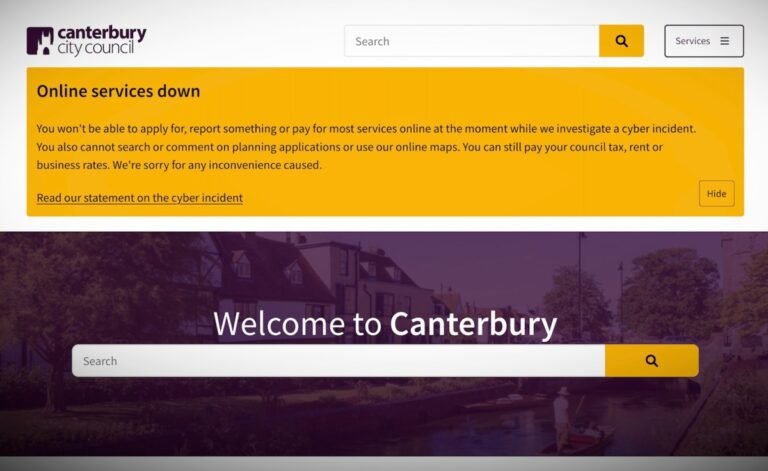
Three councils in the United Kingdom have taken some of their public-facing systems offline due to an ongoing cybersecurity issue.
The NCSC and the three councils declined to say whether the cybersecurity issue relates to an in-house system or an outside vendor.
TechCrunch found that some of Canterbury City Council’s payments systems, provided by EKS, were unavailable.
Dover and Thanet are also both reporting issues with online forms and online payments.
Since 2018, outsourcing giant Civica has provided EKS services as part of a seven-year deal to cut costs across the three councils.

LoanDepot customers say they have been unable to make mortgage payments or access their online accounts following a suspected ransomware attack on the company last week.
Users on social media and forums discussing the incident say they have struggled to access their account information or submit payments.
LoanDepot’s updating cyber incident page says several LoanDepot customer portals returned online as of Thursday, albeit with limited functionality.
When reached by email, LoanDepot spokesperson Jonathan Fine declined to comment, but did not dispute that the incident was linked to ransomware.
LoanDepot has not yet updated regulators on the company’s recovery since its initial disclosure to the SEC on January 8.

VF Corp., the parent company of the popular apparel brands Vans, Supreme, and The North Face, said Thursday that hackers stole the personal data of 35.5 million customers in a December cyberattack.
The Denver, Colorado-based company reported the data breach to regulators in a filing on Thursday.
The filing did not say specifically what kinds of personal data was taken, or if the company yet knows what was stolen.
VF Corp. spokesperson Colin Wheeler did not respond to an email from TechCrunch requesting more information.
VF Corp. previously said the hackers disrupted its operations “by encrypting some IT systems,” implying a ransomware attack.

When reached by email, LoanDepot spokesperson Jonathan Fine reiterated the company’s statement, but declined to comment further or say whether the company has received a ransom demand from the hackers.
LoanDepot says it assists more than 27,000 customers monthly.
A November ransomware attack on Fidelity National Financial, one of the largest insurance providers in the United States, knocked the company offline for more than a week.
In December, mortgage and loan company Mr. Cooper said hackers had stolen the personal data on more than 14 million customers during an earlier October cyberattack.
You can contact Zack Whittaker on Signal and WhatsApp at +1 646-755-8849, or by email.

An international law firm that works with companies affected by security incidents has experienced its own cyberattack that exposed the sensitive health information of hundreds of thousands of data breach victims.
San Francisco-based Orrick, Herrington & Sutcliffe said last week that hackers stole the personal information and sensitive health data of more than 637,000 data breach victims from a file share on its network during an intrusion in March 2023.
Orrick also said it notified health insurance company MultiPlan, behavioral health giant Beacon Health Options (now known as Carelon) and the U.S. Small Business Administration that their data was also compromised in Orrick’s data breach.
The data also includes medical treatment and diagnosis information, insurance claims information — such as the date and costs of services — and healthcare insurance numbers and provider details.
The number of individuals known to be affected by this data breach has risen by threefold since Orrick first disclosed the incident.

Here we go again: 2023’s badly handled data breaches Delays, silence and unanswered questions follow these organizations into the new yearLast year, we compiled a list of 2022’s most poorly handled data breaches looking back at the bad behavior of corporate giants when faced with hacks and breaches.
That included everything from downplaying the real-world impact of spills of personal information and failing to answer basic questions.
Samsung won’t say how many customers hit by year-long data breachSamsung has once again made it onto our badly handled breaches list.
Lyca Mobile later admitted a data breach, in which unnamed attackers had accessed “at least some of the personal information held in our system” during the hack.
Data leaked by the gang, and reviewed by TechCrunch, included the personal data of thousands of CommScope employees, including full names, postal addresses, email addresses, personal numbers, Social Security numbers, passport scans and bank account information.













