
In an effort to help businesses prevent cyberattacks, Google announced updates to its Apigee service, which includes improvements to the way business logic is protected. The new features include automated detection and prevention of malicious code execution, as well as better mocking and testing capabilities forAPI development.
Business logic attacks are incredibly difficult to detect, and can result in some serious financial damages for companies. They typically occur when faulty code triggers unintended actions as a result of how it is executed, often without the user being aware of what’s happening. This makes business logic attacks particularly tricky to spot — and extremely common.
As Google Cloud begins to deploy machine learning models that are designed to detect business logic attacks, it is important for companies to keep in mind that these models are not perfect. While they may be sensitive enough to detect subtle behavior, they can also miss more obvious attacks. It is important for companies to have an understanding of how their data is being used by these models in order to stay safe from malicious actors.
Google’s artificial intelligence models have been used to keep its public-facing APIs secure, and they rely on years of learning and best practices. By using these models, Google has been able to detect and prevent potential API abuse, ensuring that its users are safe.
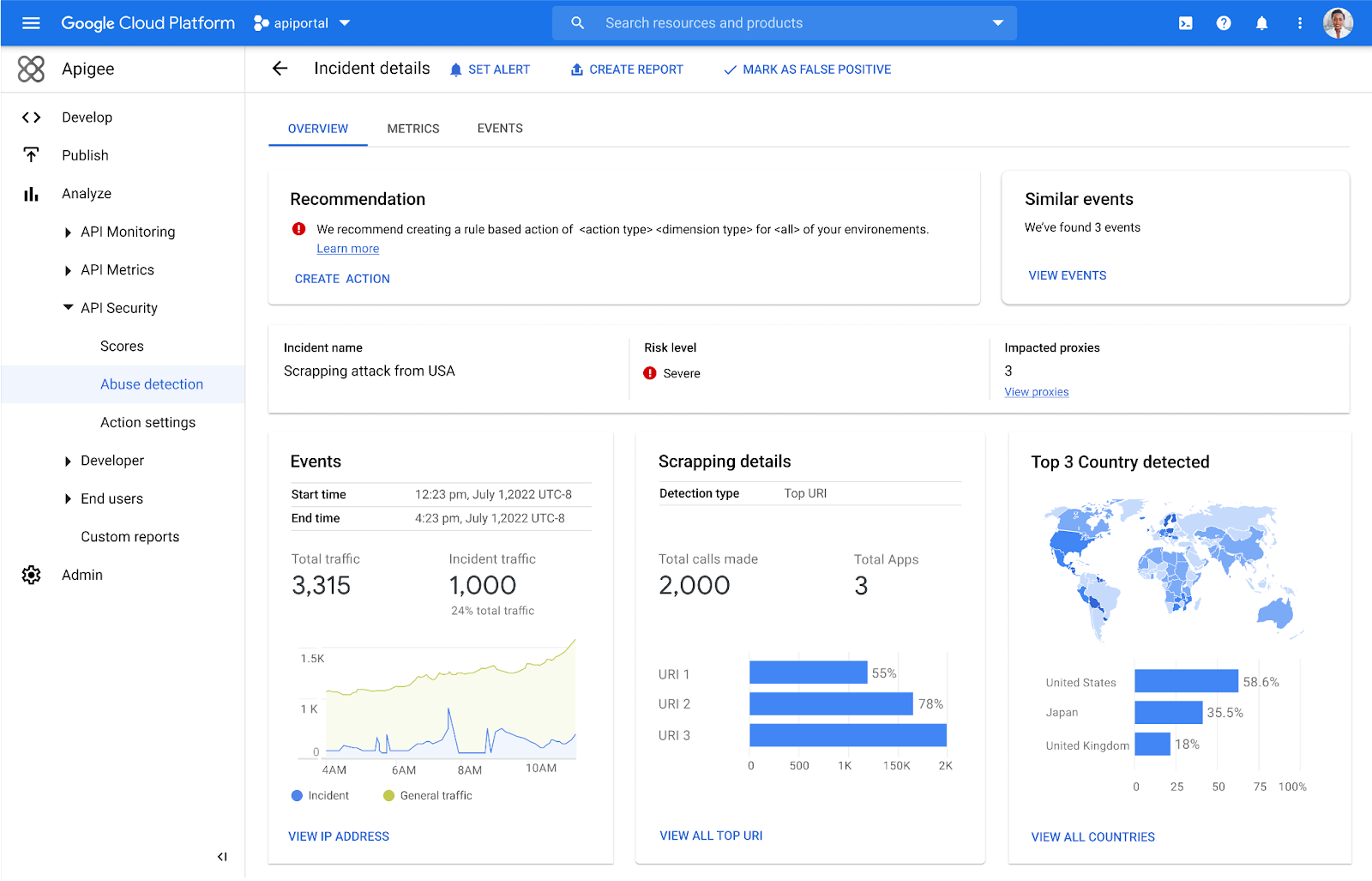
Apigee claims that its dashboards are more accurate at identifying API abuses because they take into account the number of API calls and duration of the attack. The company contends that this type of information is essential to understanding how attackers are targeting specific APIs, which can help prevent future attacks.
API security is vital for any business that depends on third-party APIs. Hershkovitz announced a new product to make it easier and faster to detect API abuse incidents. This product, called API Hammer, uses machine learning algorithms to analyze and identify malicious activity.
Digital marketing has come a long way in recent years. With so many different channels of communication available to businesses, it can be difficult to
As concerns over API security continue to grow, businesses must take measures to ensure their APIs remain secure. One way to do this is by regularly monitoring for and responding to threats, as well as engaging in multi-layered authentication and authentication management. Additionally, making sure your APIs are well-documented can help ensure developers follow your guidelines closely.
Many businesses fear that exposing their APIs, or application programming interfaces, could lead to a security breach. However, these attacks can be costly and damaging both to the company’s reputation and bottom line.
Organizations need to be careful when creating and exposing their APIs lest they suffer from security incidents. This is especially true as developers are often quick to rollout new services and apps following a security incident, resulting in decreased customer satisfaction.
Abuse of APIs can be costly for businesses – not just in terms of dollars, but also in terms of reputation. Detection and mitigation of API abuse incidents are crucial to preventing prolonged damage.








