
Even ransomware gangs fail to patch vulnerabilitiesYes, even ransomware gangs are slow to patch software bugs.
Lockbit ransomware group administrative staff has confirmed with us their websites have been seized.
pic.twitter.com/SvpbeslrCd — vx-underground (@vxunderground) February 19, 2024Ransomware takedowns take a long timeThe LockBit takedown, known officially as “Operation Cronos,” was years in the making, according to European law enforcement agency Europol.
Given Kondratiev has hands in at least five different ransomware gangs, the sanctions are likely to make his life five times more difficult.
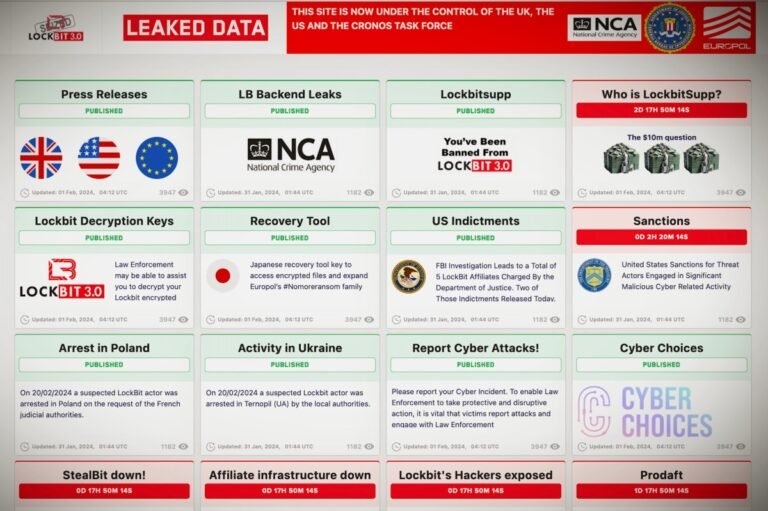
We found various Easter eggs hidden on the now-seized LockBit site.
The U.S. government has sanctioned two key members of LockBit, the Russian-speaking hacking and extortion gang accused of launching ransomware attacks against victims across the U.S. and internationally.
The U.S. sanctions announced Tuesday are the latest round of actions targeting the hackers behind LockBit and other prolific ransomware gangs.
In 2022, Russian-Canadian dual national Mikhail Vasiliev was arrested on allegations of launching multiple LockBit ransomware attacks.
A third suspect, Russian national Mikhail Pavlovich Matveev, was accused of involvement in several ransomware operations, including LockBit.
Security researchers say that ransomware victims who pay a ransom are more likely to experience subsequent ransomware attacks.

A coalition of international law enforcement agencies, including the FBI and the U.K.’s National Crime Agency, have disrupted the operations of the prolific LockBit ransomware gang.
LockBit’s dark-web leak site — where the group publicly lists its victims and threatens to leak their stolen data unless a ransom demand is paid — was replaced with a law enforcement notice on Monday.
“This site is now under the control of the National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos,’ the message reads.
The group last year claimed responsibility for attacks against aerospace giant Boeing, chipmaker TSMC, and U.K. postal giant Royal Mail.
Monday’s takedown is the latest in a series of law enforcement actions targeting ransomware gangs.

Why are ransomware gangs making so much money?
2023 was a lucrative year for ransomware gangs, fueled by an escalation in threats and tacticsFor many organizations and startups, 2023 was a rough year financially, with companies struggling to raise money and others making cuts to survive.
While 2023 was overall a bumper year for ransomware gangs, other hacker-watchers observed a drop in payments toward the end of the year.
Record-breaking ransomsWhile more ransomware victims are refusing to line the pockets of hackers, ransomware gangs are compensating for this drop in earnings by increasing the number of victims they target.
The company also predicts that a ransom payments ban would lead to the overnight creation of a large illegal market for facilitating ransomware payments.

The U.S. government sanctioned a Russian national for allegedly playing a “pivotal role” in the ransomware attack against Australian health insurance giant Medibank that exposed the sensitive information of almost 10 million patients.
The breach is believed to have impacted several high-profile Medibank customers, including senior Australian government lawmakers.
The U.S. Treasury Department sanctioned Ermakov shortly after the Australian government imposed first-of-its-kind sanctions against the Russian national.
According to the U.S. Treasury, REvil ransomware has been deployed on approximately 175,000 computers worldwide, garnering at least $200 million in ransom payments.
The FSB’s surprise operation came just months after the U.S. Department of Justice charged a 22-year-old Ukrainian citizen linked to the REvil ransomware gang due to his alleged role in the Kaseya attack.

LoanDepot customers say they have been unable to make mortgage payments or access their online accounts following a suspected ransomware attack on the company last week.
Users on social media and forums discussing the incident say they have struggled to access their account information or submit payments.
LoanDepot’s updating cyber incident page says several LoanDepot customer portals returned online as of Thursday, albeit with limited functionality.
When reached by email, LoanDepot spokesperson Jonathan Fine declined to comment, but did not dispute that the incident was linked to ransomware.
LoanDepot has not yet updated regulators on the company’s recovery since its initial disclosure to the SEC on January 8.

When reached by email, LoanDepot spokesperson Jonathan Fine reiterated the company’s statement, but declined to comment further or say whether the company has received a ransom demand from the hackers.
LoanDepot says it assists more than 27,000 customers monthly.
A November ransomware attack on Fidelity National Financial, one of the largest insurance providers in the United States, knocked the company offline for more than a week.
In December, mortgage and loan company Mr. Cooper said hackers had stolen the personal data on more than 14 million customers during an earlier October cyberattack.
You can contact Zack Whittaker on Signal and WhatsApp at +1 646-755-8849, or by email.

This year was no different to last: we saw another round of high-profile busts, arrests, sanctions, and prison time for some of the most prolific cybercriminals in recent years.
Twitter took drastic measures to rid the hackers from its network by temporarily blocking all of the site’s 200-million-plus users from posting.
A New York judge sentenced the 24-year-old hacker to five years in prison, two of which O’Connor already served in pre-trial custody.
Federal prosecutors this year accused a former Amazon employee of hacking into a cryptocurrency exchange and stealing millions worth of customers’ crypto.
Why did a Russian man accused by U.S. prosecutors of ransomware attacks burn his passport?

Statista, meanwhile, reports that a whopping over two-thirds — 72% — of businesses have been affected by ransomware attacks as of 2023.
Certainly, one vendor, Halcyon, is experiencing a boon, having raised $44 million in a Series A round last April.
The startup’s now closed a smaller Series B tranche — $40 million — that brings its total raised to $84 million.
“The Halcyon platform is built to keep businesses operational even in the event of a widespread ransomware incident,” Miller said.
“Halcyon is the only company solely focused on battling ransomware with layers for both prevention and resilience,” Miller said.
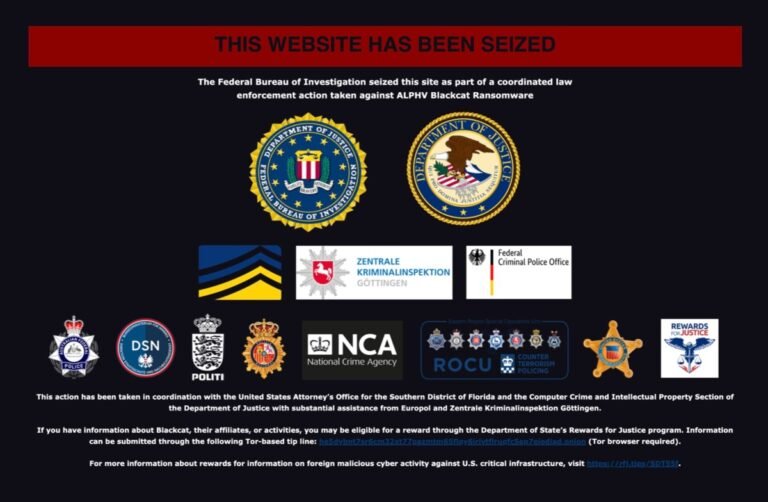
An international group of law enforcement agencies have seized the dark web leak site of the notorious ransomware gang known as ALPHV, or BlackCat.
“The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV Blackcat Ransomware,” a message on the gang’s dark web leak site now reads, seen by TechCrunch.
According to the splash, the takedown operation also involved law enforcement agencies from the United Kingdom, Germany and Australia.
Spokespeople for the FBI and the U.K.’s National Crime Agency did not immediately respond to TechCrunch’s requests for comment.
The ALPHV/BlackCat ransomware gang has been one of the most active and destructive in recent years.













